Continuing to formalize channels amongst distinct market actors, governments, and law enforcements, while still protecting the decentralized mother nature of copyright, would advance quicker incident response and strengthen incident preparedness.
Because the window for seizure at these stages is amazingly smaller, it calls for effective collective action from regulation enforcement, copyright expert services and exchanges, and Worldwide actors. The more time that passes, the more challenging Restoration gets.
help it become,??cybersecurity measures may perhaps develop into an afterthought, particularly when companies deficiency the money or personnel for such steps. The challenge isn?�t distinctive to those new to small business; nonetheless, even nicely-founded firms might Enable cybersecurity drop to the wayside or may well lack the instruction to grasp the quickly evolving danger landscape.
These risk actors had been then capable of steal AWS session tokens, the short term keys that enable you to ask for short term credentials to the employer?�s AWS account. By hijacking Energetic tokens, the attackers have been capable of bypass MFA controls and obtain entry to Protected Wallet ?�s AWS account. By timing their attempts to coincide With all the developer?�s regular function hrs, Additionally they remained undetected until finally the actual heist.
By finishing our Superior verification process, you might obtain access to OTC buying and selling and elevated ACH deposit and withdrawal restrictions.
Additional stability steps from both Protected Wallet or copyright would have reduced the chance of the incident taking place. As an example, implementing pre-signing simulations would've allowed workforce to preview the place of a transaction. Enacting delays for large withdrawals also would've presented copyright time for you to evaluation the transaction and freeze the resources.
On February 21, 2025, here when copyright workforce went to approve and sign a program transfer, the UI confirmed what appeared to be a genuine transaction While using the intended vacation spot. Only once the transfer of resources towards the concealed addresses established by the malicious code did copyright personnel know something was amiss.
Securing the copyright sector have to be manufactured a precedence if we prefer to mitigate the illicit funding with the DPRK?�s weapons systems.
The entire process of laundering and transferring copyright is costly and consists of fantastic friction, several of which is deliberately created by legislation enforcement plus some of it's inherent to the marketplace structure. As a result, the full reaching the North Korean govt will tumble much underneath $1.5 billion.
Welcome to copyright.US. This tutorial will allow you to produce and validate your own account to be able to begin shopping for, marketing, and trading your preferred cryptocurrencies very quickly.
four. Examine your telephone for the 6-digit verification code. Click on Permit Authentication following confirming that you have the right way entered the digits.
Some cryptocurrencies share a blockchain, though other cryptocurrencies operate on their own individual blockchains.
Danger warning: Getting, marketing, and Keeping cryptocurrencies are functions that happen to be issue to high market risk. The volatile and unpredictable nature of the price of cryptocurrencies may result in a substantial reduction.
On top of that, it seems that the threat actors are leveraging revenue laundering-as-a-provider, provided by structured crime syndicates in China and countries in the course of Southeast Asia. Use of this company seeks to even more obfuscate funds, cutting down traceability and seemingly using a ?�flood the zone??tactic.
In just a couple of minutes, it is possible to join and entire Standard Verification to accessibility many of our most favored characteristics.}
 Mason Gamble Then & Now!
Mason Gamble Then & Now!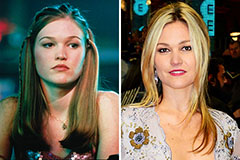 Julia Stiles Then & Now!
Julia Stiles Then & Now!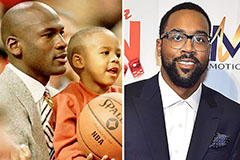 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Nancy Kerrigan Then & Now!
Nancy Kerrigan Then & Now! Rachael Leigh Cook Then & Now!
Rachael Leigh Cook Then & Now!